Millions Stolen Through Office365 Executive Email Compromise: FBI Investigation
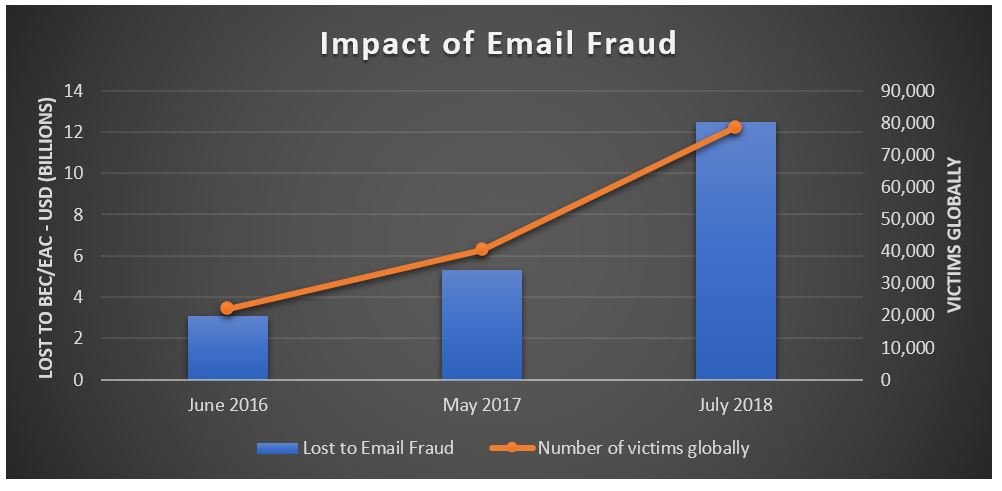
Table of Contents
The Modus Operandi of Office365 BEC Scams
Cybercriminals are employing increasingly sophisticated methods to execute these BEC attacks, leveraging the trusted nature of Office365 to their advantage.
Sophisticated Phishing Techniques
These attacks go far beyond simple spam emails. They utilize advanced techniques:
- Spear phishing: Attackers meticulously research their targets, crafting personalized emails that appear to come from trusted sources, such as colleagues, superiors, or even clients.
- Impersonation of executives: Criminals expertly mimic the communication style and email addresses of high-ranking executives to deceive employees.
- Compromised accounts: Hackers may gain access to legitimate accounts, using them to send fraudulent requests that appear completely authentic.
These emails often bypass typical spam filters due to their personalized nature and the use of legitimate email addresses and domains. Attackers often exploit vulnerabilities in email security systems.
Targeting High-Level Executives
Executives are the prime targets for BEC scams due to several factors:
- Access to sensitive financial information: Executives often have authorization to approve large transactions.
- Authority to approve transactions: Their approval is often the final step before funds are transferred.
- Reduced suspicion: Executives are less likely to scrutinize emails requesting urgent financial actions, assuming legitimacy due to the sender's apparent authority.
The psychological manipulation involved relies on urgency and trust, exploiting the executive’s position and responsibilities.
The Role of Office365 in the Attacks
Attackers cleverly exploit various Office365 vulnerabilities:
- Weak passwords: Easily guessed or stolen passwords provide an entry point.
- Lack of multi-factor authentication (MFA): MFA significantly reduces the risk of unauthorized access.
- Insufficient employee training: Employees unaware of phishing tactics are vulnerable.
- Compromised accounts: Once an account is compromised, it becomes a tool for launching further attacks.
Compromised accounts are then used to send seemingly legitimate payment requests or transfer funds directly.
The FBI Investigation and its Findings
The FBI investigation highlights a disturbing trend impacting businesses of all sizes.
Scale of the Problem
The sheer scale of the problem is alarming:
- Number of victims: The FBI reports a significant increase in reported cases of Office365 BEC scams.
- Amount of money stolen: Millions of dollars have been stolen globally through these attacks.
- Geographic spread: These attacks are not geographically limited; businesses worldwide are affected.
Precise statistics are often withheld for investigative reasons, but the impact is undeniably substantial.
Key Tactics Used by Cybercriminals
The FBI investigation reveals specific attack vectors:
- Urgent payment requests: Emails demanding immediate payment for purported invoices or emergency situations.
- W-2 phishing: Requests for employee W-2 forms to facilitate identity theft and tax fraud.
- Vendor impersonation: Fraudulent requests disguised as payments to legitimate vendors.
Criminals launder the stolen funds through complex international money transfer networks, making tracing and recovery challenging.
FBI Recommendations for Prevention
The FBI strongly recommends proactive measures:
- Implement multi-factor authentication (MFA): This adds an extra layer of security, significantly hindering unauthorized access.
- Comprehensive employee training: Regular security awareness training is essential.
- Enhanced email security measures: Employ advanced threat protection and email authentication protocols (like SPF, DKIM, and DMARC).
These recommendations emphasize a multi-layered approach to security, combining technological solutions with human vigilance.
Protecting Your Organization from Office365 BEC Attacks
Proactive measures are crucial to mitigate the risk of BEC attacks.
Strengthening Email Security
Several steps significantly bolster your Office365 security:
- Implement multi-factor authentication (MFA): This is the single most effective way to prevent unauthorized access.
- Utilize advanced threat protection: Advanced features can identify and block malicious emails.
- Regularly update software: Keep your Office365 software and operating systems up-to-date with security patches.
- Implement strong password policies: Enforce complex, unique passwords and encourage password managers.
Employee Training and Awareness
Invest in thorough and ongoing employee training:
- Regular security awareness training: Educate employees about phishing tactics and social engineering techniques.
- Phishing simulations: Conduct regular simulations to test employee awareness and response.
- Clear reporting procedures: Establish easy-to-use methods for employees to report suspicious emails.
A strong security awareness culture is your first line of defense.
Implementing Robust Verification Processes
Never rely solely on emails for financial transactions:
- Multiple points of verification: Verify all payment requests through multiple channels (phone calls, independent email confirmations).
- Independent confirmation of requests: Always confirm the legitimacy of requests with the purported sender directly, using known contact information.
These verification steps add crucial layers of protection against fraudulent requests.
Conclusion
The FBI investigation into Office365 executive email compromise scams reveals a serious and growing threat, resulting in significant financial losses for businesses worldwide. The sophistication of these attacks underscores the need for a robust, multi-layered security approach. Don't become another victim. Proactively implement strong security measures, including multi-factor authentication, advanced threat protection, and comprehensive employee training. Protecting your business from Office365 BEC scams is an investment in your future. Learn more about securing your organization against these increasingly prevalent email compromise attacks today.

Featured Posts
-
 From Federal To State Local Navigating The Job Search After Layoffs
Apr 28, 2025
From Federal To State Local Navigating The Job Search After Layoffs
Apr 28, 2025 -
 Analyzing The U S Dollars Performance A Look At The First 100 Days Under The Current Presidency
Apr 28, 2025
Analyzing The U S Dollars Performance A Look At The First 100 Days Under The Current Presidency
Apr 28, 2025 -
 Denise Richards Husband Creditor Demands Bank Statements
Apr 28, 2025
Denise Richards Husband Creditor Demands Bank Statements
Apr 28, 2025 -
 Posthaste How A Canadian Travel Boycott Impacts The Us Economy
Apr 28, 2025
Posthaste How A Canadian Travel Boycott Impacts The Us Economy
Apr 28, 2025 -
 Shop The Hudsons Bay Liquidation Huge Markdowns On Everything
Apr 28, 2025
Shop The Hudsons Bay Liquidation Huge Markdowns On Everything
Apr 28, 2025
