Millions Lost: Executive Office365 Accounts Targeted In Major Data Breach
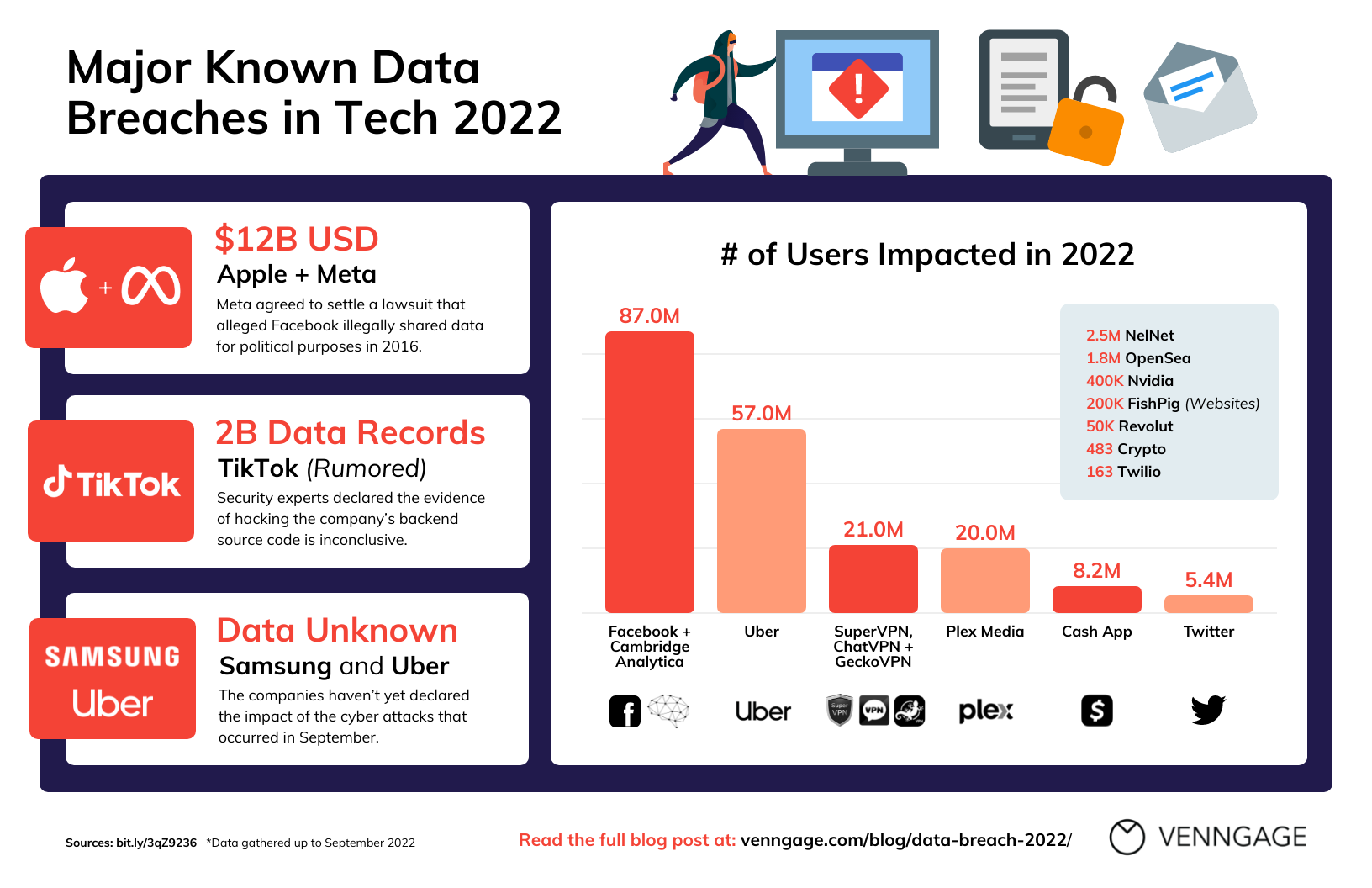
Table of Contents
The Scale of the Breach: Understanding the Impact
This data breach represents a significant escalation in the targeting of high-profile accounts. The sheer scale of the attack underscores the devastating consequences that can result from compromised executive-level access.
Number of Affected Accounts:
- Estimate: While the exact number remains undisclosed for security reasons, credible sources suggest the breach affected tens of thousands, potentially reaching into the hundreds of thousands, of executive Office365 accounts globally.
- Geographical Distribution: The affected accounts span numerous countries, indicating a widespread and coordinated attack. The geographic reach demonstrates the attackers' ambition and the global nature of this threat.
- Organizations Affected: The breach impacted a diverse range of organizations, including Fortune 500 companies, government agencies, and significant players in various industries. This lack of industry specificity underlines the indiscriminate nature of the attack.
Data Compromised:
The consequences of this breach extend far beyond simple password resets. Attackers potentially gained access to incredibly sensitive information, impacting both the organizations and the individuals involved.
- Examples of Compromised Data: The leaked data likely includes emails containing confidential strategic plans, sensitive financial records, intellectual property, and personal information of executives and employees. Access to these executive inboxes opens pathways to many other sensitive systems.
- Potential Consequences: Data exposure of this magnitude can result in significant financial losses due to fraud, intellectual property theft, and legal liabilities. Reputational damage, loss of investor confidence, and severe disruption to business operations are also likely outcomes. For individuals, identity theft and financial scams are significant concerns.
Vulnerabilities Exploited: How the Attack Happened
Understanding how the attackers gained access is crucial to implementing effective preventative measures. This breach likely leveraged a combination of sophisticated techniques.
Phishing and Social Engineering:
The initial compromise likely stemmed from expertly crafted phishing attacks and sophisticated social engineering tactics.
- Common Phishing Tactics: Spear phishing, tailored to target specific individuals within organizations, was likely employed. This includes highly convincing fake login pages designed to mimic legitimate Office365 interfaces. The attackers may have researched their targets extensively to increase the likelihood of success.
- Success Rate: The success of these attacks underscores the efficacy of well-crafted phishing campaigns and the vulnerability of users despite security awareness training. Even experienced professionals can fall victim to such targeted attacks.
Exploited Software Vulnerabilities:
While specific vulnerabilities haven't been publicly disclosed, it's highly probable that the attackers exploited known or zero-day vulnerabilities within the Office365 ecosystem or associated third-party applications.
- Unpatched Software: Outdated software and applications are prime targets for exploitation. Many vulnerabilities are quickly identified and patched by developers, making regular updates essential.
- Importance of Patching: Promptly installing security updates and patches is paramount in mitigating the risk of such attacks. Automated update mechanisms significantly reduce the window of vulnerability.
Weak Passwords and Authentication Issues:
Weak or reused passwords, coupled with a lack of robust authentication protocols, significantly weakened the organizations' security posture.
- Strong, Unique Passwords: The importance of using strong, unique passwords for each account cannot be overstated. Password managers can help in generating and securely storing complex passwords.
- Multi-Factor Authentication (MFA): Implementing multi-factor authentication (MFA) is no longer optional; it's a necessity. MFA adds an extra layer of security, significantly reducing the risk of unauthorized access even if credentials are compromised.
Protecting Your Office365 Account: Essential Security Measures
Proactive security measures are vital to safeguarding your Office365 environment. Implementing these strategies can dramatically reduce your organization's vulnerability.
Implementing Multi-Factor Authentication (MFA):
MFA is your first line of defense against unauthorized access.
- MFA Methods: Explore various MFA options, including time-based one-time passwords (TOTP), authenticator apps (like Google Authenticator or Authy), security keys, and biometric authentication.
- Setting up MFA: Microsoft provides detailed instructions on enabling MFA for Office365. Ensure that all executive and high-privilege accounts utilize MFA.
Regularly Updating Software and Patches:
Keeping your software updated is crucial in mitigating security risks.
- Checking for Updates: Regularly check for updates to Office365, operating systems, and all applications used in conjunction with Office365.
- Automated Updates: Configure automatic updates wherever possible to ensure that systems are consistently patched against the latest vulnerabilities.
Advanced Threat Protection:
Investing in advanced threat protection tools significantly enhances your security posture.
- Advanced Threat Protection Features: Look for solutions offering advanced anti-phishing, anti-malware, and sandboxing capabilities. These tools can detect and neutralize sophisticated threats that traditional security measures might miss.
- Office365 Security Resources: Microsoft offers various advanced threat protection solutions integrated with Office365. Explore the options to determine which best fit your organization's needs.
Security Awareness Training for Employees:
Educating employees is crucial in preventing phishing attacks and other social engineering attempts.
- Training Programs: Implement regular security awareness training programs that cover common threats like phishing, social engineering, and safe password practices.
- Benefits of Training: Well-trained employees are the first line of defense against many cyberattacks. Regular training reinforces good security habits and improves their ability to identify and report suspicious activities.
Conclusion
The massive Office365 data breach affecting millions of executive accounts serves as a stark reminder of the ever-present threat of cyberattacks. The scale of this breach underscores the critical need for robust cybersecurity measures. By implementing multi-factor authentication, regularly updating software, investing in advanced threat protection, and providing comprehensive security awareness training, organizations can significantly reduce their vulnerability to similar attacks. Don't wait for a similar incident to affect your organization. Secure your Office365 accounts today and protect your valuable data from malicious actors. Take control of your Office365 security now and prevent becoming another statistic in the next major data breach.

Featured Posts
-
 Sophie Nyweide Child Actor In Mammoth And Noah Dies At 24
Apr 24, 2025
Sophie Nyweide Child Actor In Mammoth And Noah Dies At 24
Apr 24, 2025 -
 Political Backlash Impacts Tesla Q1 Earnings Reveal 71 Net Income Fall
Apr 24, 2025
Political Backlash Impacts Tesla Q1 Earnings Reveal 71 Net Income Fall
Apr 24, 2025 -
 The Value Of Middle Managers Benefits For Companies And Employees
Apr 24, 2025
The Value Of Middle Managers Benefits For Companies And Employees
Apr 24, 2025 -
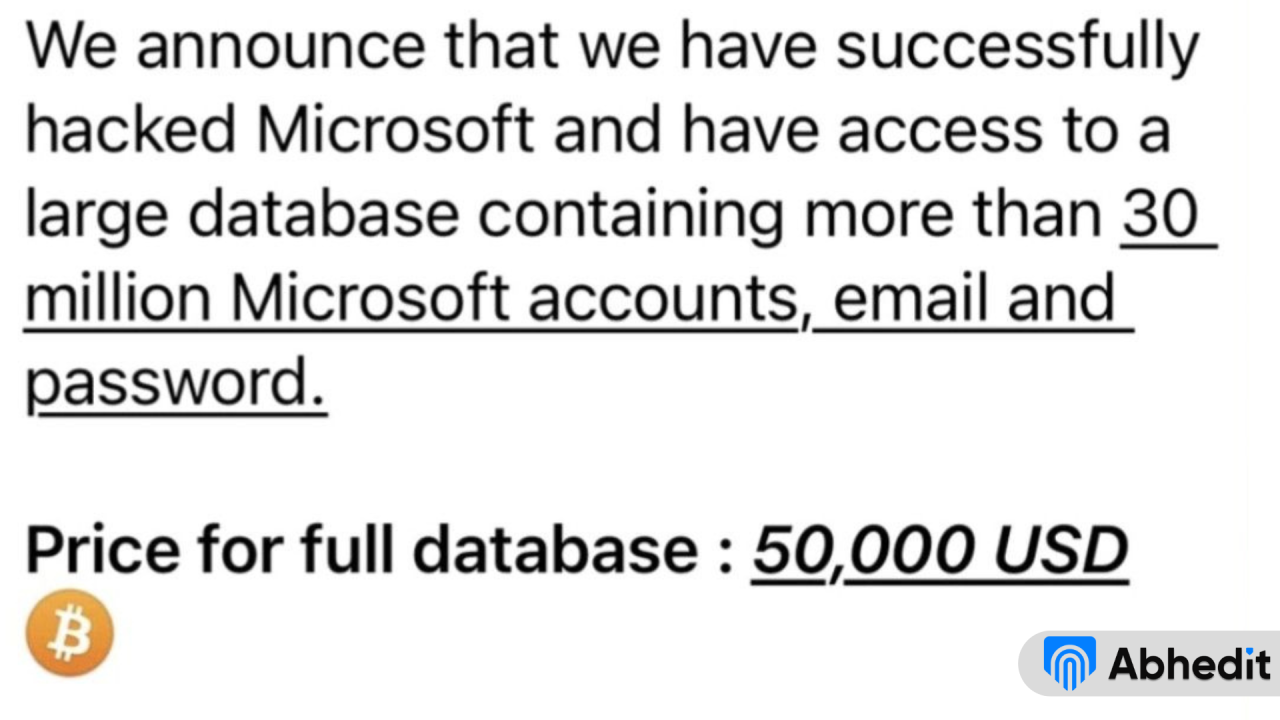 Federal Investigation Into Multi Million Dollar Office365 Data Breach
Apr 24, 2025
Federal Investigation Into Multi Million Dollar Office365 Data Breach
Apr 24, 2025 -
 John Travolta Shares Personal Photo Calms Fan Anxiety
Apr 24, 2025
John Travolta Shares Personal Photo Calms Fan Anxiety
Apr 24, 2025
