Federal Investigation Into Multi-Million Dollar Office365 Data Breach
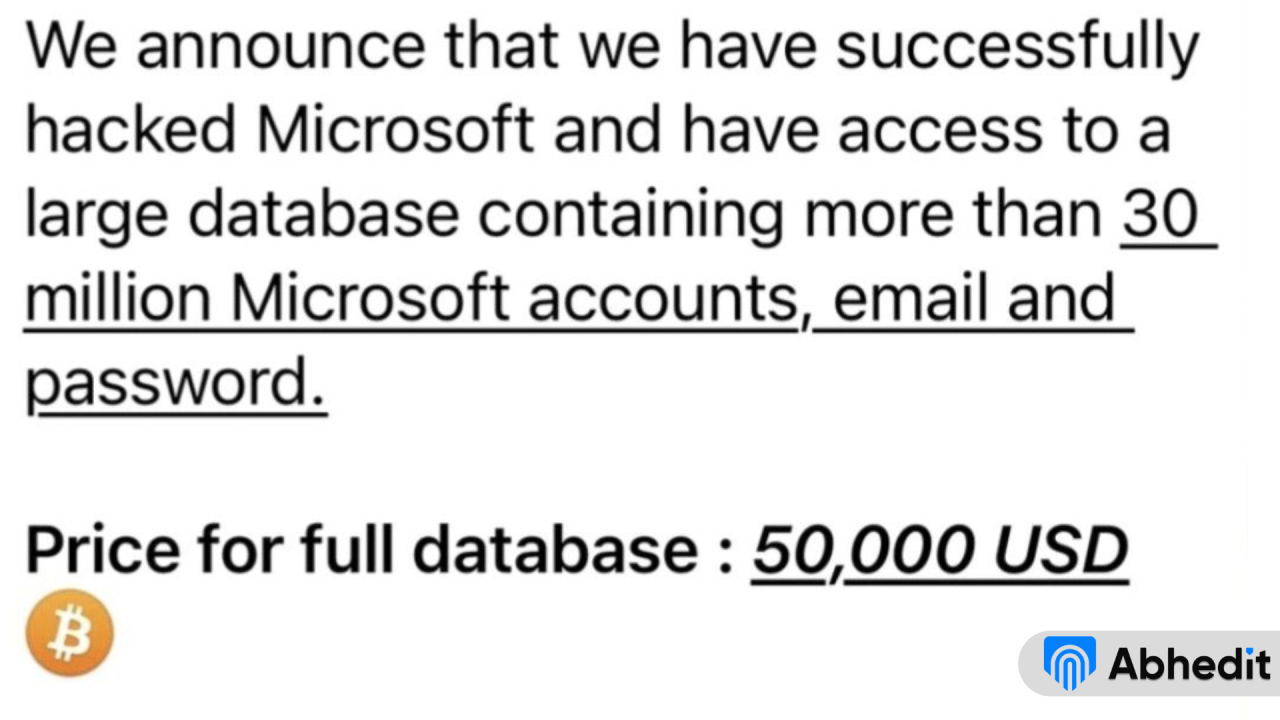
Table of Contents
The Scope of the Office365 Data Breach
This Office365 data breach represents a significant threat to data security, impacting numerous businesses and individuals. Understanding its scope is crucial to implementing effective preventative measures.
Financial Losses and Affected Parties
The exact financial losses are still being assessed, but early estimates suggest a multi-million dollar impact. The breach affected a wide range of organizations, including government agencies dealing with sensitive citizen information, healthcare providers handling protected health information (PHI), and financial institutions managing sensitive financial data. While specific details about affected parties remain confidential during the ongoing investigation, the sheer breadth of impacted sectors underscores the severity of the situation. The economic fallout extends beyond direct financial losses to include the costs of remediation, legal fees, and reputational damage.
Types of Data Compromised
The data compromised in this breach included a range of sensitive information. This potentially includes:
- Customer Information: Names, addresses, email addresses, phone numbers, and in some cases, credit card details.
- Employee Records: Personally Identifiable Information (PII), social security numbers, and other sensitive employee data.
- Intellectual Property: Confidential business documents, trade secrets, and proprietary information.
- Financial Data: Bank account details, transaction records, and other sensitive financial information.
The scale of the data loss is staggering, potentially exposing millions of individuals and organizations to identity theft, financial fraud, and other serious risks.
- Specific examples of compromised data types are currently under investigation and cannot be publicly released at this time to protect the ongoing investigation.
- The precise number of individuals and organizations affected is still being determined by investigating agencies.
- Affected parties are spread across multiple geographic locations within the United States.
The Federal Investigation's Progress
A comprehensive federal investigation is underway, led by a coalition of key agencies dedicated to uncovering the truth and holding perpetrators accountable.
Investigating Agencies Involved
Several federal agencies are actively involved, including the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA). The FBI is focusing on identifying and apprehending the individuals responsible for the attack, while CISA is concentrating on assessing the vulnerabilities exploited and providing guidance to prevent future breaches. Other agencies may be involved depending on the specific nature of the compromised data and the affected parties.
Investigation Methods and Techniques
Investigators are employing a multifaceted approach, utilizing advanced forensic techniques to analyze compromised systems and trace the source of the attack. This includes:
- Forensic analysis: Analyzing computer systems, network logs, and other digital evidence to reconstruct the attack and identify the perpetrators.
- Interviews: Gathering information from affected parties and individuals who may have knowledge of the breach.
- Data tracing: Tracking the movement of stolen data to identify potential accomplices or recipients of the stolen information.
At the time of writing this article, no arrests or indictments have been publicly announced.
- The investigation is ongoing, and a detailed timeline of key events will be released as appropriate.
- Public statements regarding the progress of the investigation are expected to be released periodically by the involved agencies.
- Potential legal repercussions for those responsible could include significant fines, imprisonment, and other penalties.
Vulnerabilities Exploited and Lessons Learned
Understanding the vulnerabilities exploited in this Office365 data breach is critical for preventing similar incidents.
Identifying the Root Cause
While the full details are still emerging from the ongoing federal investigation, initial reports suggest that the attackers may have exploited common vulnerabilities, such as:
- Phishing Attacks: Deceptive emails designed to trick users into revealing their login credentials.
- Weak Passwords: Easily guessable or reused passwords that are easily cracked by attackers.
- Unpatched Software: Outdated software with known security flaws that could be exploited.
These vulnerabilities highlight the critical need for robust security protocols and employee training.
Best Practices for Preventing Similar Breaches
To prevent future Office365 data breaches, organizations should implement the following best practices:
-
Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security to user accounts, making it much harder for attackers to gain unauthorized access.
-
Regular Software Updates: Ensure all software, including Office365 applications, is regularly updated to patch security vulnerabilities.
-
Employee Cybersecurity Awareness Training: Train employees to recognize and avoid phishing attempts and other social engineering attacks.
-
Strong Password Policies: Enforce strong, unique passwords and encourage the use of password managers.
-
Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities in your systems.
-
Implementing strong password policies and utilizing MFA could have significantly mitigated the risk.
-
Regular security awareness training could have helped employees recognize and avoid phishing attempts.
-
Resources for cybersecurity training and best practices are readily available from reputable sources like CISA and Microsoft.
Conclusion
The multi-million dollar Office365 data breach underscores the critical importance of robust cybersecurity practices. This federal investigation highlights the significant financial and reputational risks associated with data breaches and the urgent need for organizations to prioritize data security. The types of data compromised, the ongoing investigation, and the vulnerabilities exploited all underscore the necessity for proactive measures. Strengthen your Office365 security today by implementing the best practices outlined in this article. Learn more about protecting your data from Office365 breaches and implement preventative measures to avoid a costly Office365 data breach. Take control of your cybersecurity posture and protect your valuable data.

Featured Posts
-
 The Bold And The Beautiful Spoilers Wednesday April 23 Finns Vow To Liam
Apr 24, 2025
The Bold And The Beautiful Spoilers Wednesday April 23 Finns Vow To Liam
Apr 24, 2025 -
 Over The Counter Birth Control A Post Roe Game Changer
Apr 24, 2025
Over The Counter Birth Control A Post Roe Game Changer
Apr 24, 2025 -
 Ray Epps Sues Fox News For Defamation January 6th Allegations At The Center Of The Lawsuit
Apr 24, 2025
Ray Epps Sues Fox News For Defamation January 6th Allegations At The Center Of The Lawsuit
Apr 24, 2025 -
 Saudi Arabia And India Partner To Build Two New Oil Refineries
Apr 24, 2025
Saudi Arabia And India Partner To Build Two New Oil Refineries
Apr 24, 2025 -
 New Google Fi 35 Unlimited Plan A Detailed Review
Apr 24, 2025
New Google Fi 35 Unlimited Plan A Detailed Review
Apr 24, 2025
