Cybercriminal Makes Millions From Compromised Executive Office365 Accounts
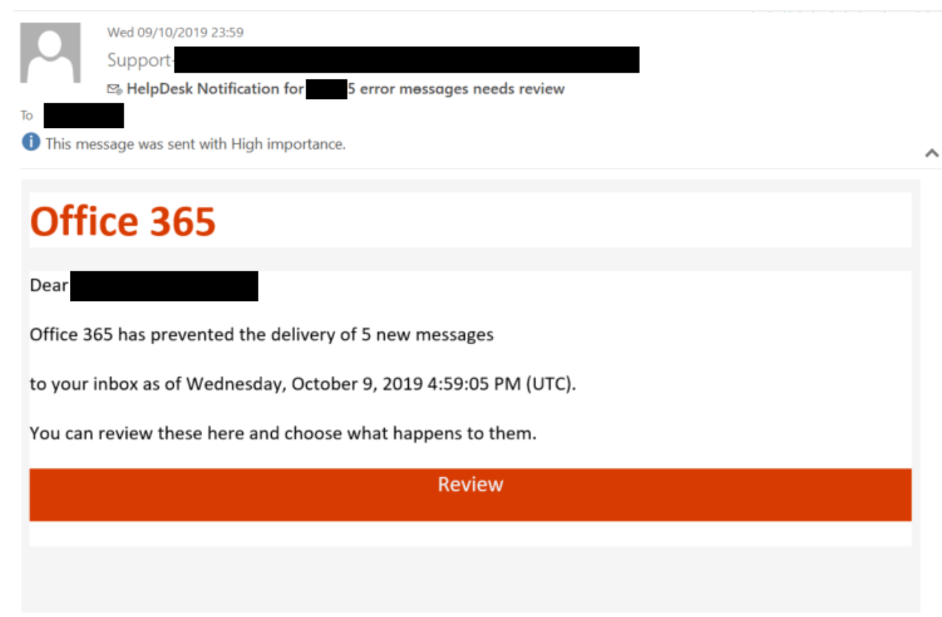
Table of Contents
The Modus Operandi of Executive Office365 Account Compromise
Cybercriminals employ increasingly sophisticated methods to compromise executive Office365 accounts, resulting in significant financial losses and reputational damage. Their strategies often combine social engineering with technical exploits, targeting the weakest link: human error.
Phishing and Spear Phishing Attacks
Phishing and spear phishing attacks remain the most common entry point for attackers. These emails are meticulously crafted to appear legitimate, often mimicking trusted sources like banks or internal communications.
- Examples of phishing email subject lines: "Urgent Payment Required," "Confidential Information," "Security Alert."
- Common lures: Requests for urgent payments, demands for sensitive information, or notifications of supposed account issues.
- Social engineering tactics: Creating a sense of urgency, exploiting trust, and using personalized details gleaned from social media or public records to increase believability.
- These attacks can sometimes bypass multi-factor authentication (MFA) through techniques like SIM swapping or phishing for MFA codes.
Exploiting Software Vulnerabilities
Attackers also exploit vulnerabilities in Office365 and related applications. Outdated software and unpatched systems create significant entry points for malicious actors.
- Outdated software: Failure to update applications and operating systems leaves systems vulnerable to known exploits.
- Unpatched systems: Ignoring security patches allows attackers to exploit known vulnerabilities.
- Weak passwords: Simple or easily guessable passwords are easily cracked through brute-force attacks.
- Attackers leverage these vulnerabilities to gain unauthorized access, installing malware or exploiting backdoors.
Credential Stuffing and Brute-Force Attacks
Credential stuffing and brute-force attacks are automated methods used to gain access to accounts. These attacks rely on lists of stolen usernames and passwords obtained from previous data breaches.
- How these attacks work: Attackers use automated tools to try various combinations of usernames and passwords against target accounts.
- Effectiveness against weak passwords: Weak passwords are easily cracked, making accounts vulnerable to these attacks.
- Importance of password managers and strong password policies: Utilizing password managers and implementing strong password policies (length, complexity, and regular changes) are crucial preventative measures.
The Financial Ramifications of Compromised Executive Accounts
The financial consequences of compromised executive Office365 accounts can be devastating, leading to substantial losses and long-term damage.
Wire Transfer Fraud
Attackers often use compromised accounts to initiate fraudulent wire transfers, targeting large sums of money.
- Examples of successful attacks: Attackers impersonating executives to authorize large payments to fraudulent accounts.
- Speed at which funds are moved: Funds are often transferred quickly, making recovery difficult.
- Difficulty in recovering stolen funds: Recovering funds after a fraudulent wire transfer can be extremely challenging, requiring extensive legal and investigative efforts.
Data Theft and Extortion
The theft of sensitive business information, including financial records, strategic plans, and customer data, can lead to extortion or insider trading.
- Types of data targeted: Financials, strategic plans, customer lists, intellectual property.
- Long-term consequences of data breaches: Reputational damage, loss of customer trust, legal liabilities, regulatory fines.
- Reputational damage: Data breaches can severely damage an organization's reputation and lead to long-term financial losses.
Ransomware Attacks
Compromised accounts can be used to deploy ransomware, encrypting critical data and demanding payment for its release.
- Costs associated with ransomware attacks: Ransom payments, data recovery costs, business downtime, legal fees.
- Impact on business operations: Ransomware attacks can severely disrupt business operations, leading to significant financial losses and operational disruptions.
Protecting Your Executive Office365 Accounts from Compromise
Protecting executive Office365 accounts requires a multi-layered approach that combines robust security measures, employee training, and advanced security tools.
Implementing Robust Security Measures
Implementing strong security measures is the first line of defense against these attacks.
- Multi-factor authentication (MFA): MFA adds an extra layer of security, requiring multiple forms of authentication to access accounts.
- Strong password policies: Enforce complex, unique passwords that are regularly changed.
- Regular security awareness training for employees: Educate employees about phishing scams and other social engineering tactics.
- Email security solutions (spam filters, advanced threat protection): Employ robust email security solutions to filter out malicious emails and detect advanced threats.
- Regular software updates and patching: Keep all software and operating systems up-to-date with the latest security patches.
The Role of Security Awareness Training
Security awareness training is critical in preventing successful phishing attacks.
- Simulations: Conduct regular phishing simulations to test employee awareness and identify vulnerabilities.
- Regular training: Provide ongoing training on identifying and reporting phishing attempts.
- Clear communication protocols: Establish clear protocols for reporting suspicious emails and security incidents.
Utilizing Advanced Security Tools
Advanced security tools can provide additional layers of protection.
- Advanced threat protection: Detect and prevent advanced persistent threats (APTs) that can bypass traditional security measures.
- Security information and event management (SIEM) systems: Collect and analyze security logs from various sources to detect and respond to security incidents.
- Intrusion detection/prevention systems (IDS/IPS): Monitor network traffic for malicious activity and block attempts to compromise systems.
Conclusion
The compromise of executive Office365 accounts poses a significant threat to organizations, leading to substantial financial losses and reputational damage. Attackers use a combination of phishing, software vulnerabilities, and automated attacks to gain access. The resulting wire transfer fraud, data theft, and ransomware attacks can cripple businesses. To protect your organization, implementing robust security measures, including multi-factor authentication, strong password policies, regular security awareness training, and advanced security tools, is crucial. Ignoring these precautions leaves your executive accounts, and your entire organization, vulnerable to significant financial loss from Office365 compromise. Don't wait until it's too late; invest in comprehensive cybersecurity solutions and employee training today. If you need assistance, seek professional cybersecurity advice to bolster your defenses against this growing threat.

Featured Posts
-
 Alberta Feels The Impact Dow Project Delay And Tariff Fallout
Apr 28, 2025
Alberta Feels The Impact Dow Project Delay And Tariff Fallout
Apr 28, 2025 -
 Yukon Legislature Threatens Contempt Proceedings Against Mine Manager
Apr 28, 2025
Yukon Legislature Threatens Contempt Proceedings Against Mine Manager
Apr 28, 2025 -
 Red Sox Injury Updates For Crawford Bello Abreu And Rafaela
Apr 28, 2025
Red Sox Injury Updates For Crawford Bello Abreu And Rafaela
Apr 28, 2025 -
 A Comprehensive Look At The Luigi Mangione Support Base
Apr 28, 2025
A Comprehensive Look At The Luigi Mangione Support Base
Apr 28, 2025 -
 Xs Financial Reorganization Insights From Musks Recent Debt Sale
Apr 28, 2025
Xs Financial Reorganization Insights From Musks Recent Debt Sale
Apr 28, 2025
