Office 365 Executive Inbox Breaches Net Millions For Crook, FBI Says
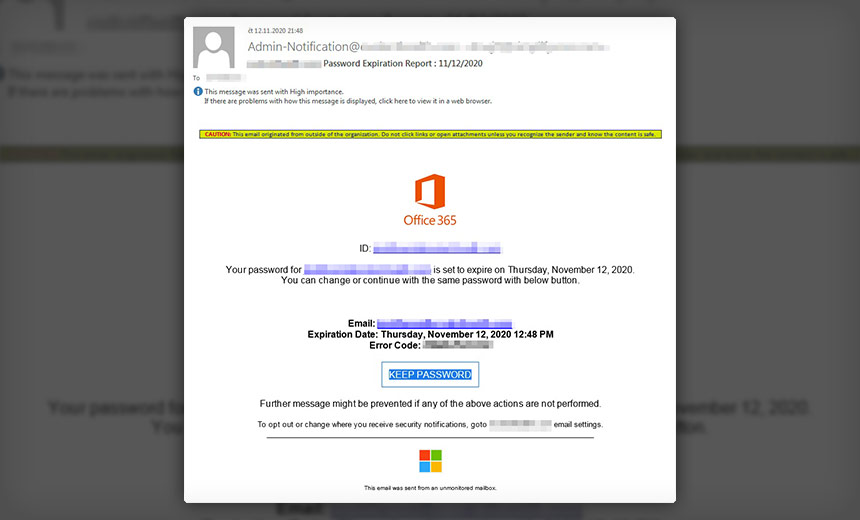
Table of Contents
The FBI Investigation: Unveiling the Methods of the Attack
The FBI's investigation uncovered a sophisticated and meticulously planned cyberattack targeting executive email accounts within the Office 365 ecosystem. The criminals employed a multi-pronged approach, combining advanced techniques to gain unauthorized access and pilfer sensitive financial information.
- Sophisticated Phishing Campaigns: The attackers utilized highly targeted phishing emails designed to mimic legitimate communications from trusted sources. These emails often contained malicious links or attachments designed to deliver malware or steal credentials.
- Credential Stuffing Attacks: Stolen credentials from other breaches were used in brute-force attacks against Office 365 accounts. Attackers systematically attempted to log in using combinations of usernames and passwords obtained from previous data leaks.
- Exploiting Software Vulnerabilities: The investigation revealed that attackers exploited known vulnerabilities in older, unpatched versions of Office 365 applications and related software. This allowed them to bypass security controls and gain access to accounts.
The scale of the financial losses is staggering, with millions of dollars stolen from multiple victims. The FBI is currently pursuing leads and working to apprehend those responsible for this widespread cybercrime. Keywords: FBI cybercrime, Office 365 phishing, account takeover, credential compromise, advanced persistent threat (APT), cybersecurity investigation
Understanding the Vulnerabilities Exploited in Office 365
Attackers exploited several weaknesses in Office 365 security protocols, highlighting the importance of a multi-layered security approach. These vulnerabilities often stem from human error and a lack of proactive security measures.
- Weak Passwords: Many executive accounts utilized easily guessable passwords, making them vulnerable to brute-force attacks and credential stuffing.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA significantly weakened account security, allowing attackers to bypass password-based authentication even if they obtained the correct credentials.
- Unpatched Software: Outdated software versions contain known vulnerabilities that attackers can exploit to gain unauthorized access. Failing to apply regular updates exposes organizations to significant risks.
- Insufficient Employee Training: A lack of employee awareness regarding phishing scams and social engineering techniques makes them more susceptible to falling prey to malicious actors.
These entry points underscore the need for a comprehensive security strategy that encompasses technical safeguards and employee training. Keywords: Office 365 vulnerabilities, MFA (multi-factor authentication), password security, software updates, security patches, email security best practices
Protecting Your Organization from Similar Office 365 Breaches
Protecting your organization from similar Office 365 breaches requires a proactive and multifaceted approach. Implementing the following measures can significantly reduce your risk:
- Implement Strong Password Policies and Multi-Factor Authentication (MFA): Enforce strong password policies that require complex passwords and regular changes. Mandatory MFA adds an extra layer of security, preventing unauthorized access even if credentials are compromised.
- Regularly Update Software and Patches: Keep all Office 365 applications and related software up-to-date with the latest security patches to mitigate known vulnerabilities.
- Train Employees on Phishing Awareness and Social Engineering Tactics: Conduct regular security awareness training to educate employees on identifying and reporting suspicious emails and avoiding social engineering tactics.
- Utilize Advanced Threat Protection Tools: Implement advanced threat protection solutions that can detect and block malicious emails and attachments before they reach users' inboxes.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities in your systems and address them proactively. This helps in identifying weaknesses before attackers do.
These steps are crucial to creating a robust defense against sophisticated cyberattacks targeting Office 365. Keywords: Office 365 security best practices, cybersecurity training, threat intelligence, email security solutions, data loss prevention (DLP), incident response plan
The Long-Term Impact and Economic Consequences of Office 365 Breaches
The consequences of an Office 365 breach extend far beyond the immediate financial losses. Organizations face significant long-term repercussions, including:
- Reputational Damage: A data breach can severely damage an organization's reputation, leading to loss of customer trust and impacting brand loyalty.
- Legal Liabilities: Data breaches can result in significant legal liabilities, including fines and lawsuits under regulations like GDPR and CCPA.
- Loss of Customer Trust: Compromised data can lead to a loss of customer trust, impacting future business opportunities and potentially causing long-term financial damage.
- Increased Cybersecurity Costs: Responding to and recovering from a breach involves substantial costs, including incident response, legal fees, and remediation efforts.
The increasing frequency and sophistication of cyberattacks highlight the critical need for robust cybersecurity measures. Keywords: cybersecurity costs, reputational risk, legal compliance, data protection regulations, GDPR, CCPA
Conclusion
The FBI investigation into the multi-million dollar Office 365 executive inbox breaches underscores the critical vulnerability of even the most secure-seeming systems. The attackers used sophisticated techniques like phishing, credential stuffing, and exploiting software vulnerabilities to gain access and steal significant financial resources. To prevent similar breaches, organizations must prioritize proactive security measures. This includes implementing strong password policies, mandatory multi-factor authentication, regular software updates, comprehensive employee training, and advanced threat protection tools. Strengthen Office 365 security by assessing your current posture and taking immediate steps to improve it. Ignoring these vulnerabilities could lead to significant financial losses, reputational damage, and legal liabilities. Consult with cybersecurity experts to develop a robust security strategy and prevent future Office 365 breaches. Improve email security and secure your executive inboxes today.

Featured Posts
-
 Trumps Uncommon Rebuke Putin Faces Criticism After Kyiv
Apr 25, 2025
Trumps Uncommon Rebuke Putin Faces Criticism After Kyiv
Apr 25, 2025 -
 The Chinese Automotive Market Challenges And Opportunities For International Brands
Apr 25, 2025
The Chinese Automotive Market Challenges And Opportunities For International Brands
Apr 25, 2025 -
 Coalition Politics In Montana Democrats And Republicans Fight For Senate Majority
Apr 25, 2025
Coalition Politics In Montana Democrats And Republicans Fight For Senate Majority
Apr 25, 2025 -
 Tramp I Ukraina Beliy Dom Oprovergaet Plany Vizita
Apr 25, 2025
Tramp I Ukraina Beliy Dom Oprovergaet Plany Vizita
Apr 25, 2025 -
 Veteran Runner Bob Fickel Prepares For 40th Canberra Marathon
Apr 25, 2025
Veteran Runner Bob Fickel Prepares For 40th Canberra Marathon
Apr 25, 2025
