Execs' Office 365 Accounts Targeted: Millions Stolen, Authorities Report
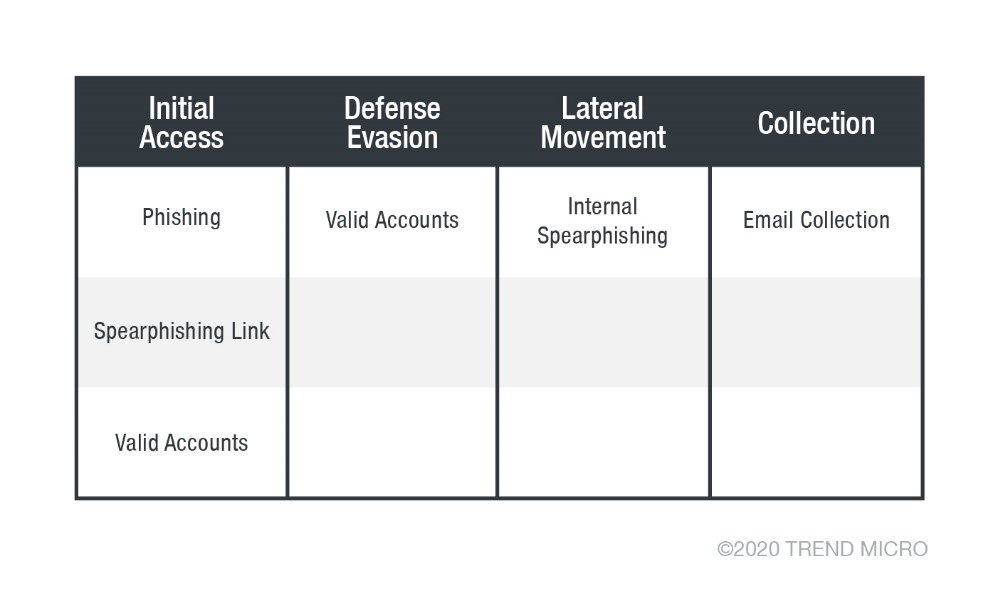
Table of Contents
The Scale and Scope of the Office 365 Executive Account Breaches
The scale of the Office 365 executive account breaches is alarming. While precise figures remain elusive due to many attacks going unreported, reports suggest millions of accounts have been compromised globally. The attacks are not geographically confined; they span various regions and sectors, impacting businesses of all sizes and across numerous industries. The targets are often high-ranking executives, including CEOs, CFOs, CIOs, and other C-suite personnel, whose access to sensitive information makes them particularly valuable to cybercriminals.
- Specific numbers of compromised accounts: While precise figures are not consistently reported publicly due to the sensitive nature of the breaches, industry estimations suggest millions of accounts have been affected.
- Industries most affected: Financial services, technology, healthcare, and manufacturing are frequently targeted due to the valuable intellectual property and sensitive data they possess.
- Geographic areas most impacted: While global in scope, certain regions with higher concentrations of businesses and advanced digital infrastructure see more frequent attacks.
- Examples of high-profile companies affected: While specific companies rarely publicly acknowledge breaches involving executive accounts due to reputational damage concerns, reports indicate that both large multinational corporations and smaller businesses have fallen victim.
Attack Methods Used in Compromising Office 365 Executive Accounts
Cybercriminals employ increasingly sophisticated techniques to breach Office 365 executive accounts. These attacks often leverage a combination of methods, exploiting both vulnerabilities in the platform and weaknesses in human behavior. Common tactics include:
- Phishing and Spear Phishing: These attacks use deceptive emails or messages designed to trick users into revealing their credentials or downloading malware. Spear phishing targets specific individuals with highly personalized and convincing messages.
- Credential Stuffing: Attackers use stolen credentials from other data breaches to try and access Office 365 accounts. This brute-force approach can be surprisingly effective if users reuse passwords across multiple platforms.
- Malware: Malicious software, such as keyloggers and Trojans, can be used to steal credentials, monitor activity, and exfiltrate sensitive data from compromised accounts. This often occurs through cleverly disguised attachments or links within phishing emails.
- Zero-Day Exploits: While less common, the exploitation of previously unknown software vulnerabilities (zero-day exploits) can grant attackers direct access to Office 365 accounts without relying on user interaction.
The Impact of Compromised Executive Office 365 Accounts
The consequences of compromised executive Office 365 accounts are far-reaching and severe. These breaches can lead to:
- Data Theft: Financial records, intellectual property, strategic plans, confidential communications, and customer data can all be stolen, leading to significant financial losses and reputational damage.
- Financial Loss: Direct financial losses from theft, ransom demands, and the costs of remediation and legal action can be substantial.
- Reputational Damage: Breaches erode trust with customers, partners, and investors, potentially leading to long-term damage to the organization's reputation.
- Legal and Regulatory Fines: Non-compliance with data protection regulations like GDPR can result in hefty fines and legal repercussions.
- Blackmail and Extortion: Access to sensitive information can be leveraged for blackmail or extortion purposes.
- Insider Threats: Compromised accounts can be used to facilitate insider threats, as attackers can gain access to internal systems and sensitive data.
Protecting Executive Office 365 Accounts: Best Practices and Prevention
Protecting executive Office 365 accounts requires a multi-layered approach encompassing both technological and human factors. Key strategies include:
- Multi-Factor Authentication (MFA): Enabling MFA adds an extra layer of security, requiring users to provide multiple forms of authentication, significantly reducing the risk of unauthorized access.
- Strong and Unique Passwords: Encourage the use of long, complex, and unique passwords for all accounts, utilizing password managers to help manage them securely.
- Security Awareness Training: Regular security awareness training for all employees, especially executives, is crucial to educate them about phishing scams, malware threats, and best security practices.
- Advanced Threat Protection: Invest in advanced threat protection solutions that offer real-time threat detection and response capabilities. This can include features such as anti-phishing, anti-malware, and intrusion detection systems.
- Regular Security Audits and Vulnerability Assessments: Conduct regular security audits and vulnerability assessments to identify and address any weaknesses in your organization's security posture.
Step-by-step guide to enabling MFA: Most Office 365 accounts offer MFA through a straightforward process outlined in their admin settings. This typically involves linking a mobile authenticator app or enabling email verification codes.
Conclusion: Safeguarding Your Executives' Office 365 Accounts
The scale of attacks targeting execs' Office 365 accounts is a serious concern, with potentially devastating consequences for organizations and individuals alike. The impact of a breach extends far beyond immediate data loss, affecting reputation, finances, and legal compliance. Proactive security measures are not optional; they are essential for protecting sensitive information and preventing significant damage. Don't become another statistic – take immediate action to secure your executives' Office 365 accounts today. Implement multi-factor authentication, strengthen password policies, invest in advanced threat protection, and provide robust security awareness training. Your organization's future depends on it. For more resources on securing your Office 365 environment, visit [link to relevant resource].

Featured Posts
-
 India Trip Turns Usha Vance Into An Unlikely Celebrity
Apr 25, 2025
India Trip Turns Usha Vance Into An Unlikely Celebrity
Apr 25, 2025 -
 12
Apr 25, 2025
12
Apr 25, 2025 -
 Blue Origin Rocket Launch Postponed Subsystem Malfunction
Apr 25, 2025
Blue Origin Rocket Launch Postponed Subsystem Malfunction
Apr 25, 2025 -
 Auto Dealerships Push Back On Mandatory Ev Sales
Apr 25, 2025
Auto Dealerships Push Back On Mandatory Ev Sales
Apr 25, 2025 -
 Matthew Golden A First Round Option For The Dallas Cowboys
Apr 25, 2025
Matthew Golden A First Round Option For The Dallas Cowboys
Apr 25, 2025
