Cybercriminal's Office365 Exploit Nets Millions, Authorities Reveal
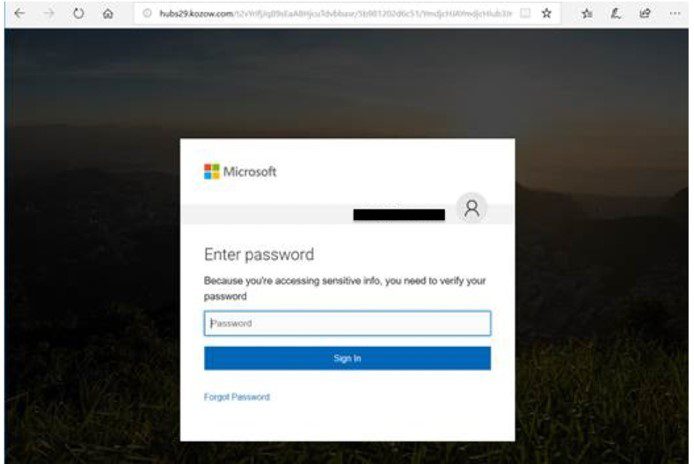
Table of Contents
The Method Behind the Millions: Uncovering the Office365 Exploit
The cybercriminals behind this million-dollar cyberattack employed a multi-pronged approach, leveraging sophisticated techniques to gain access to sensitive data and financial resources. Their success highlights the need for layered security and proactive measures to prevent similar breaches.
Phishing Campaigns as the Initial Vector
The initial attack vector was a series of meticulously crafted phishing emails designed to trick unsuspecting employees into compromising their Office365 accounts. These emails were remarkably deceptive, employing various social engineering tactics to bypass security awareness training.
- Deceptive Subject Lines: Emails used urgent subject lines like "Urgent Invoice," "Payment Overdue," or impersonated legitimate business contacts.
- Malicious Attachments: Attachments included seemingly harmless documents containing malicious macros or links leading to malware downloads.
- Social Engineering Tactics: Attackers employed pressure tactics, creating a sense of urgency to force quick action and bypass careful scrutiny.
The effectiveness of these tactics stemmed from their ability to circumvent existing security measures, emphasizing the need for robust email security solutions and continuous employee training.
Exploiting Weak Passwords and Multi-Factor Authentication (MFA) Bypass
The attackers exploited a combination of weak passwords and, in some cases, successfully bypassed multi-factor authentication (MFA). This highlights a critical weakness in many organizations’ security postures.
- Weak Password Usage: A significant portion of compromised accounts utilized easily guessable passwords or reused passwords across multiple platforms. Statistics show that [insert statistic on weak password usage if available] of accounts utilize weak passwords.
- MFA Bypass Techniques: The criminals employed methods such as SIM swapping to gain control of victims' mobile devices and intercept MFA codes, demonstrating the limitations of MFA if not implemented correctly.
Implementing strong password policies, enforcing complex password requirements, and utilizing robust MFA, coupled with security awareness training to educate employees about phishing attempts, are essential to mitigating this risk.
Data Exfiltration and Ransomware Deployment
Once inside the Office365 environment, the attackers systematically accessed and exfiltrated sensitive data. In some instances, ransomware was deployed, crippling business operations and demanding hefty ransoms.
- Types of Data Stolen: Stolen data included customer data, financial records, intellectual property, and confidential business information.
- Data Exfiltration Methods: Attackers utilized various methods, including direct cloud storage access and email forwarding to steal information.
- Ransomware Demands: Victims faced ransomware demands ranging from [insert range if available], often paid in cryptocurrency to maintain anonymity.
The lasting impact of such data breaches extends far beyond monetary losses, encompassing significant reputational damage, legal repercussions, and the erosion of customer trust.
The Victims: Who was Targeted and How Extensive was the Damage?
The Office365 exploit targeted a diverse range of businesses, demonstrating the indiscriminate nature of these attacks.
Profiling the Targeted Businesses
The attackers did not appear to focus on any single industry.
- Industries Affected: Healthcare, finance, and technology companies were among the industries significantly impacted.
- Business Sizes: Both small and medium-sized enterprises (SMEs) and larger corporations were targeted, highlighting the vulnerability across the business spectrum.
The attackers likely chose their victims based on the perceived value of their data and the perceived weakness of their security defenses.
Financial and Reputational Losses
The financial losses stemming from this Office365 exploit are staggering.
- Total Financial Loss: The total financial impact is estimated at [insert estimated financial loss if available] including direct losses from data theft, ransom payments, and the costs associated with recovery and remediation.
- Reputational Damage: Companies suffered significant reputational damage, with some experiencing a decline in stock prices and a loss of customer confidence.
- Legal Repercussions: Businesses faced legal repercussions, including regulatory fines and potential lawsuits from affected customers.
These broader consequences underscore the far-reaching impact of cyberattacks beyond immediate monetary losses.
Authorities' Response and Lessons Learned
Authorities are actively investigating this cybercrime, pursuing the perpetrators and working to mitigate further damage.
Law Enforcement Investigation and Actions
[Insert details about the investigation and actions taken by law enforcement if available. Mention agencies involved and any arrests made.] The challenges involved in tracking down cybercriminals who often operate across borders and utilize anonymizing techniques are significant.
Best Practices for Office365 Security
To avoid becoming victims of similar Office365 exploits, businesses must implement robust security measures:
- Strong Password Policies: Enforce strong, unique passwords and implement password managers.
- Robust MFA Implementation: Utilize multi-factor authentication for all accounts.
- Regular Security Awareness Training: Educate employees about phishing scams and other social engineering tactics.
- Email Security Solutions: Implement advanced spam filters and anti-phishing tools.
- Data Loss Prevention (DLP) Measures: Implement DLP tools to monitor and control data movement.
- Regular Software Updates and Patching: Keep all software, including Office365, updated with the latest security patches.
Proactive measures are crucial to prevent future attacks and protect against devastating financial and reputational consequences.
Conclusion
The massive Office365 exploit, resulting in millions of dollars in losses, serves as a critical wake-up call for all businesses. The attackers’ success highlights the need for a multi-layered approach to cybersecurity, encompassing strong password policies, robust multi-factor authentication, comprehensive employee training, and advanced security solutions. Ignoring these best practices leaves your organization vulnerable to similar Office365 exploits and the devastating financial and reputational consequences they entail. Review your Office365 security protocols today and take immediate action to strengthen your defenses against cyber threats. Don't become the next victim of a costly Office365 exploit.

Featured Posts
-
 Ray Epps Sues Fox News For Defamation Jan 6th Falsehoods At The Heart Of The Case
Apr 22, 2025
Ray Epps Sues Fox News For Defamation Jan 6th Falsehoods At The Heart Of The Case
Apr 22, 2025 -
 Microsoft Activision Deal Ftc Files Appeal
Apr 22, 2025
Microsoft Activision Deal Ftc Files Appeal
Apr 22, 2025 -
 Putin Ends Ukraine Truce Renewed Conflict Erupts
Apr 22, 2025
Putin Ends Ukraine Truce Renewed Conflict Erupts
Apr 22, 2025 -
 Turning Poop Into Podcast Gold An Ai Powered Approach To Repetitive Documents
Apr 22, 2025
Turning Poop Into Podcast Gold An Ai Powered Approach To Repetitive Documents
Apr 22, 2025 -
 Ukraine Under Fire Russia Launches Deadly Air Strikes As Us Seeks Peace
Apr 22, 2025
Ukraine Under Fire Russia Launches Deadly Air Strikes As Us Seeks Peace
Apr 22, 2025
